AskApache Password Protect wordpress plugin resources analysis
| Download This Plugin | |
| Download Elegant Themes | |
| Name | AskApache Password Protect |
| Version | 4.6.10 |
| Author | askapache |
| Rating | 56 |
| Last updated | 2014-09-23 11:27:00 |
| Downloads |
117435
|
| Download Plugins Speed Test plugin for Wordpress | |
Home page
Delta: 0%
Post page
Delta: 0%
Home page PageSpeed score has been degraded by 0%, while Post page PageSpeed score has been degraded by 0%
AskApache Password Protect plugin added 2 bytes of resources to the Home page and 2 bytes of resources to the sample Post page.
AskApache Password Protect plugin added 0 new host(s) to the Home page and 0 new host(s) to the sample Post page.
Great! AskApache Password Protect plugin ads no tables to your Wordpress blog database.This is totally and completely unlike any other security plugin for WordPress. They operate at the application-level by controlling or using PHP to stop attacks, this plugin works at the network-level BEFORE PHP, which is why this plugin is so darn effective. This plugin is specifically designed to stop automated attackers attempts to exploit vulnerabilities on your blog that result in a hacked site.
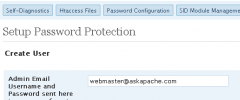
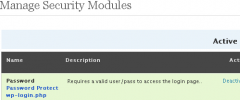
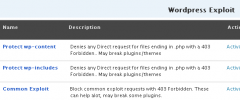
The power of this plugin is that it creates a virtual wall -- using builtin Apache Server security -- around your blog allowing it to stop attacks before they even reach your blog to deliver a malicious payload. In addition this plugin also has the capability to block spam and other malicious requests with a resounding slap, saving CPU, Memory, and Database resources. Choose a username and password to protect your entire /wp-admin/ folder and login page (or use my online htpasswd generator. Forbid common exploits and attack patterns with Mod_Security, Mod_Rewrite, Mod_Alias and Apache's tried-and-true Core Security features. Also uses the Perishable Press 5G Blacklist 2013.
This plugin requires the worlds #1 web server, Apache, and web host support for .htaccess files.
You can set up Password Protection for your blog using HTTP Basic Authentication, or you can choose to use the more secure HTTP Digest Authentication.
Read the .htaccess Guide for more information. Check out the 5G Blacklist 2013.
Has a user-contributed attack signature system modeled after the Snort Intrusion Detection and Prevention system, Nessus Vulnerability Scanner, and the Web Application Firewall ModSecurity.